Kerberos
Kerberos runs as a third-party trusted server. This topic contains information about Kerberos authentication in Windows Server 2012 and Windows 8.

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux
KerberosNET supports the KeyTable keytab file format for passing in the keys used to decrypt and validate Kerberos tickets.

Kerberos. Kerberos is the mythological three-headed Greek creature which is guarding the gates of underworld to prevent souls from escaping. According to myth Kerberos you might know him as Cerberus guards the Gates to the Underworld. It uses secret-key cryptography and a trusted third party for authenticating client.
Microsoft Kerberos Configuration Manager for SQL Server is a diagnostic tool that helps troubleshoot Kerberos related connectivity issues with SQL Server SQL Server Reporting Services and SQL Server Analysis Services. The moon was not seen in earlier Hubble images because the exposure times were shorter. That callers to a service represent a principal in the system or That a caller to a service has been granted the right to act on behalf of a principal a right which the principal can grant for a limited amount of time.
For plugin module developers. Astronomy The 4th moon of Pluto discovered in 2011. It is designed at MIT to allow network resources in a secure manner.
Kerberos is available in many commercial products as well. Kerberos is a protocol for authenticating service requests between trusted hosts across an untrusted network such as the internet. Kerberos is an authentication protocol that is used to verify the identity of a user or host.
Kerberos Alternative spelling of Cerberus An authentication protocol using a central ticket server. The Kerberos authentication protocol provides a mechanism for mutual authentication between entities before a secure network connection is established. Kerberos is a network authentication protocol.
How to build this documentation from the source. It was confirmed in subsequent Hubble pictures taken on July 3 and July 18. Contributing to the MIT Kerberos Documentation.
A free implementation of this protocol is available from the Massachusetts Institute of Technology. Kerberos Hades Gigantic Three Headed Watchdog Son of Typhon and Ekhidna said to be Hades watchdog and father of all Hellhounds whos job was that Shades didnt try to escape. It was imaged along with Pluto and its four other moons by the New Horizons spacecraft in July 2015.
Kerberos is a small natural satellite of Pluto about 19 km 12 mi in its longest dimension. Kerberos is built in to all major operating systems including Microsoft Windows Apple OS X FreeBSD and Linux. How does Kerberos work.
Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. PyKerberos Package This Python package is a high-level wrapper for Kerberos GSSAPI operations. Protocols and file formats.
With that as its inspiration the Massachusetts Institute of Technology developed a protocol to protect its own projects in the late 1980s. Hes a big 3 headed dog with a snake for a tail and a really bad temper. In this article we will see discussed the Kerberos concept and its working with the help of an example.
The goal is to avoid having to build a module that wraps the entire Kerberosframework. In Kerberos Authentication server and database is used for client authentication. In the modern world MIT Computer Scientists used the name and visual of Kerberos for.
Kerberos is a computer network authentication protocol. Κερβερος was one of the many children of Echidna and Typhon. Kerberos was discovered on June 28 2011 by a large team led by Mark Showalter using the Hubble Space Telescope.
It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. The keytab file format is. Throughout this documentation the two entities are called the client and the server even though secure network connections can be made between servers.
Kerberos is a system for authenticating access to distributed services. It was the fourth moon of Pluto to be discovered and its existence was announced on 20 July 2011. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet.
When Typhon threatened the gods Hades went into battle with Cerberus.

Artist Tomasz Jedruszek Aka Morano Title Transcendent Kerberos Card Unknown Greek Mythological Creatures Mythological Creatures Werewolf Art

Cerberus Or Kerberos In Greek And Roman Mythology Is A Multi Headed Usually Three Headed Dog Or Hel Greek And Roman Mythology Greek Mythology Greek Myths

Kerberos Gp1 Jpg Image Cops Group Pictures Jin Roh

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony

A Brief Tutorial About Kerberos And It S Integration With Cloudera Hadoop Cluster Installation Custer Security

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Cluster Dedicated Kdc Kdc On Master Node Emr Big Data Master

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Kerberos Architecture Computer Help Windows Server Microsoft
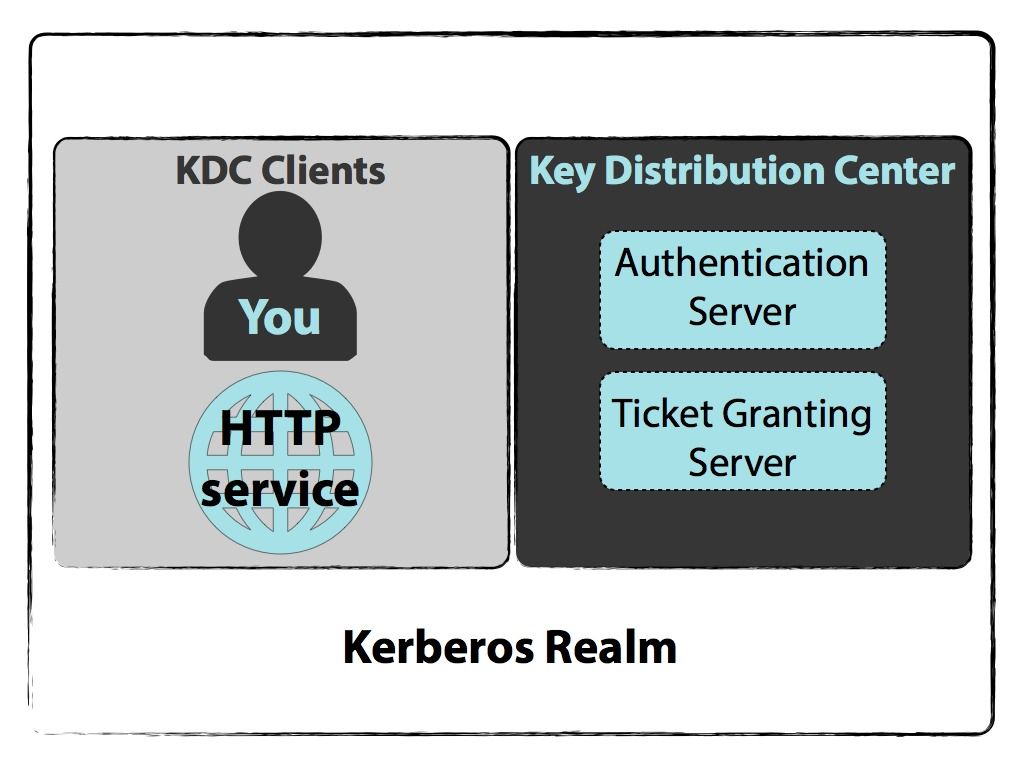
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Soldier Kerberos Panzer Cop Armor Concept Character Art Character Design

Kerberos Architecture Computer Help Windows Server Microsoft

Selecthiveql Nifi Connection Hives

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base

Kerberos Explained Security Companies Band Patches Microsoft

What Is Kerberos And How It Works Social Media Infographic Computer Network Infographic

Linux Server Das Umfassende Handbuch Inkl Samba Kerberos Datenbanken Kvm Und Docker Ansible U V M Ausgabe 2019 Handbuch Inkl Linux Bucher Samba

Post a Comment for "Kerberos"